What is DTLS?
DTLS: A quick definition
DTLS stands for Datagram Transport Layer Security. It’s a session layer communications protocol designed to protect data privacy. It allows datagram-based applications to communicate while preventing tampering, eavesdropping, and message forgery.
DTLS is based on the Transport Layer Security (TLS) protocol, which provides security to computer-based communications networks. It was developed with TLS for applications with an unreliable transport layer, such as in the case of the IoT, video conferencing, VoIP, VPN, and online gaming.
Alongside Secure Real-time Transport Protocol (SRTP), DTSL is one of the security protocols used for Web Real-Time Communication (WebRTC) technology, which includes web browsing, mail, instant messaging, and internet telephony.
The original DTLS 1.0 (defined in IETF document RFC 4347) was replaced by DTLS 1.2 (RFC 5246 and RFC 6347) and later 1.3, each based on the corresponding TLS 1 protocol version.
How does DTLS work?
A datagram (the “D” in DTLS) is a bit like a telegram, but with digital data. These data “packets” don’t require any prior connection between sender and receiver because they contain enough information to find their own way to the destination.
User Datagram Protocol (UDP) is mainly used to establish low-latency connections between applications on the internet. As UDP prioritises fast data transfer and short response times, it’s useful for time-sensitive communications like VoIP, DNS lookup, and video or audio playback.
However, with no confirmation or flow control, the connection is unreliable. The sender doesn’t know whether the message has been received, and if data packets overtake each other on route, the recipient can’t be sure they’ve arrived in the correct order. That’s where DTLS comes in.
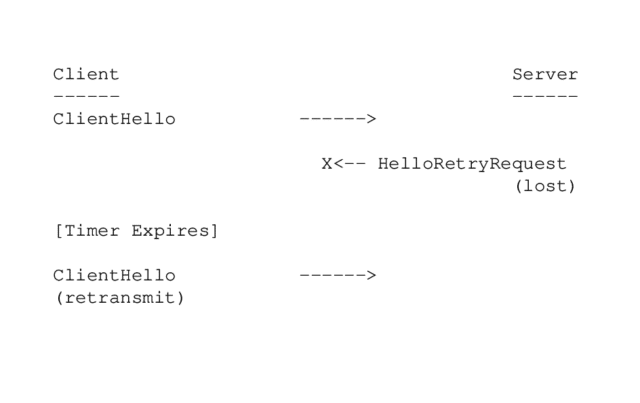
The DTLS protocol is like an extra layer of privacy for UDP communications, and it’s designed to prevent data packages from getting lost or arriving in the wrong order. DTLS uses a simple retransmission timer for this, with each endpoint continuing to retransmit its last message until a reply is received.
DTLS vs TLS
Although DTLS is based on TLS, they are two different things. Whereas DTLS is built on UDP, TLS uses Transmission Control Protocol (TCP). TLS cannot go directly on top of UDP because it’s unable to cope with the packet loss or reordering that may occur.
In this instance, the TLS handshake layer will assume that handshake messages have been delivered reliably, and will break the connection if messages get lost. Because its mission is to deliver data reliably and with end-to-end encryption via TCP, it can’t be used to secure unreliable datagram traffic.
DTLS is also designed to deliver authenticated and encrypted application data, but it enables lower latency—which means it can process a very high volume of data messages with minimal delay. As we mentioned in the previous section, DTLS solves the problems of reordering or packet loss using a retransmission timer.
TLS’s traffic encryption layer does not allow packets to be decrypted independently, since the integrity check depends on the sequence number. DTLS uses explicit (rather than implicit) sequence numbers to resolve this.
However, there are many similarities. DTLS is basically a datagram-compatible version of TLS, specifically designed so that minimal changes are required to solve the problems that TLS can’t fix. Since DTLS is so similar, pre-existing TLS protocol infrastructure and implementations can be reused.

Advantages of DTLS
Handles unreliable transport layers
When TLS (and its predecessor, SSL) was developed, most applications used TCP—so the limitations of UDP didn’t present much of a problem. But a growing number of application layer protocols have been designed to use UDP transport, including Session Initiation Protocol (SIP), Real Time Protocol (RTP), and various gaming protocols.
Users could turn to IPsec (Internet Protocol Security), but it’s not particularly suitable for client-server application models. DTLS, as we’ve seen above, is specifically built to handle unreliable transport layers, and doesn’t suffer from delays that occur with streaming protocols.
Privacy
To recap, DTLS provides top-notch security, enabling communication between client-server applications without the exchange being overheard or manipulated. This is especially useful for industries with sensitive data, such as finance and healthcare.
If you’re using a Virtual Private Network (VPN), you may find that the speed drops when a TCP connection is used within another TCP connection. Since most internet traffic is still TCP-based, it’s better to set up a UDP-based tunnel, through which DTLS will improve the performance of the VPN.
End-to-end security
DTLS uses a majority of the cipher suites described for TLS, including hash algorithms such as SHA-256, block cipher modes like AES-GCM, and the RSA public-key cryptosystem. DTLS-SRTP is typically used in WebRTC for secure media key exchange and to detect “man-in-the-middle” attacks.
When the protocol was designed, security experts kept it as close to TLS as possible, preserving much of the code and infrastructure to minimise the number of new security techniques required. This means that DTLS offers the same security guarantees as TLS, but reduces the need to use IPsec or design a custom application layer security protocol.
Because the DTLS handshake takes place over datagram transport, it’s potentially vulnerable to two denial of service (DoS) attacks: The standard resource consumption attack and the amplification attack.
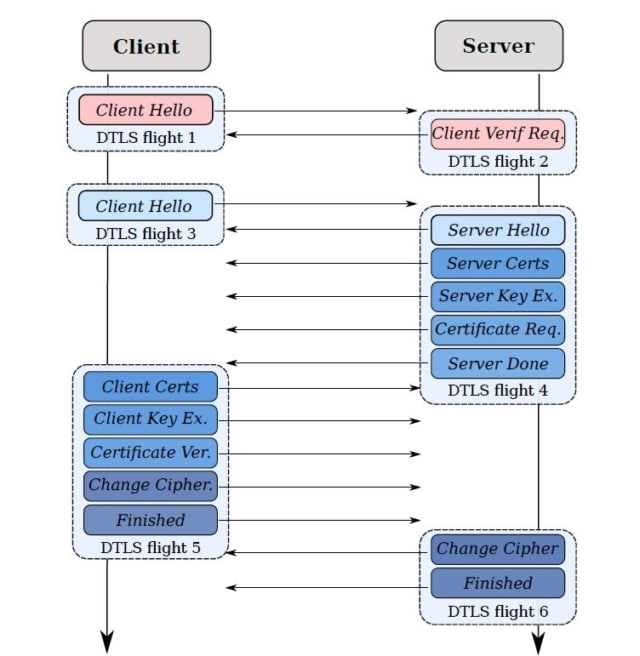
To prevent these attacks, DTLS uses the cookie exchange technique. When the client sends its ClientHello, the server responds with a HelloVerifyRequest message containing an opaque cookie. The client must send this back as a second ClientHello to demonstrate that it is not using a fake IP address.
Applications
DTLS is the ideal solution for delay-sensitive applications using datagram transport, as it’s explicitly designed to be as compatible as possible with existing datagram communication systems. So, it takes less effort for application protocol designers to secure their applications.
Internet telephony
Internet telephony, or VoIP, offers businesses a more affordable, flexible, and scalable alternative to traditional phone lines—but they need to know that communications are fully secure.
If your system is built on WebRTC (an open-source project that enables real-time communication natively from a web browser), DTLS combines with SRTP (Secure Real-time Transport Protocol) to authorise the remote party and secure sensitive data.
Thanks to specialised cipher suites and pre-shared keys, DTLS is able to work fast even on low-powered devices. This low resource consumption saves businesses money, and helps remote workers stay in touch even when their devices are unplugged.
Online gaming
DTLS is also used in online gaming, especially for Massive Multiplayer Online Games like StarCraft and Quake where low latency is essential. In fast-paced games, you can’t put up with lag—if you tell your character to do something but it takes them a few seconds to move, it could be game over.
Because DTLS runs over UDP instead of TCP, it consumes less bandwidth. This is also handy for gamers, coupled with the fact that DTLS can be used on low-powered devices.
Streaming video & audio
Low latency and the ability to fix reordering or packet loss make DTLS perfect for real-time video and audio conferencing, where any delays would be detrimental to your business. High security is also vital for business communications, especially those handling sensitive data.
RingCentral Video, for example, is built on top of WebRTC, which requires applications to employ encrypted signaling transport protocols. Data streams are encrypted using DTLS, and media streams are encrypted using SRTP.
This also means the application includes all the advantages and best practices employed by browser vendors in their security models. Plus, RingCentral also guarantees 99.999% uptime, so your video and audio calls will never let you down.
RingCentral uses DTLS for privacy and security for communication across the board
As we’ve explained in this post, DTLS implementation gives you enhanced security and privacy, as well as ensuring that high volumes of data are transmitted quickly and without packet loss or reordering.
That’s why it’s favoured by RingCentral. We’re committed to best software development practices, ensuring that our enterprise-grade applications for voice, video, and messaging are highly secure and reliable. Your business can communicate with anyone, anywhere, in the knowledge that critical data and conversations are safe.
Originally published Nov 19, 2021

