Acquiring one of Europe’s strictest data protection standard
Whether it’s sophisticated vishing scams, zoom bombing or hackers taking advantage of the vulnerabilities of mass home working, business security is in the spotlight now more than ever.
Recently, many businesses have migrated to the cloud as part of hybrid working models to facilitate collaboration for remote teams or simply to drive digital transformation for the organisation. However, the overwhelming number of cloud platforms and services on the market and increasing awareness of data use and privacy can make it difficult to identify the best-qualified providers to protect your business information.
That means it’s important to understand the risks and identify the vulnerabilities of working in the cloud. Even more crucial is choosing a cloud service provider (CSP) that offers the transparency, guidance and official credentials you need when it comes to safeguarding your business.
When it comes to clarity and transparency as part of a best-practice, standardised framework, Germany is arguably blazing the trail, not least for implementing the C5 attestation. CSPs are widely adopting this to give businesses that operate in Europe and across borders peace of mind.
What is C5?
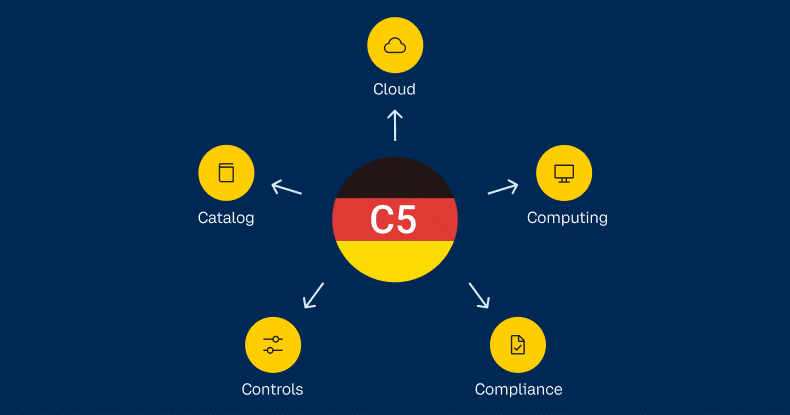
The C5 is a government-backed German verification framework implemented by the German Federal Office for Information Security (BSI). The five ‘C’s stand for Cloud, Computing, Compliance, Controls and Catalog (hence C5). The BSI introduced the framework for CSPs to demonstrate effective security and mitigate cyber-attacks when using their cloud-based services.
Introduced in 2016 and updated in 2020, in response to the ever-changing technology landscape, the BSI introduced the framework as a way to rigorously assess the levels of security of cloud services in the context of the German Government’s “Security Recommendations for Cloud Providers”.

Why does the C5 exist?
The overall objective of C5 is to increase the transparency of data protection in the cloud as organisations move away from traditional application and infrastructure responsibilities.
It helps cloud users know whether a cloud service provider has fulfilled their requirements. These requirements can include:
- Securing the authorisation and authentication of users to prevent unauthorised access
- Timeliness and reliability of access to and use of data
- Tracking of changes and transactions without adversely affecting their execution
- Safeguards to protect against malicious attacks
- Reviewing and managing operational workflow
Who is the C5 relevant for?
As of October 2020, the C5 was a mandated requirement in Germany for those providing cloud services to government agencies, but compliance is not restricted to German-based cloud service providers. The fact that many cloud service providers have sought to obtain the C5 compliance verification suggests that private sector organisations are set to take steps to obtain this stringent level of security.
Internationally recognised frameworks and standards are increasing in demand, particularly for businesses that operate or trade across borders. Businesses with operations in Europe will want to consider the benefits of adopting a C5 accredited cloud service provider (CSP).
C5 benefits any organisation looking for a belt-and-braces approach to its security standards that safeguards its business information and customer data. The verification is relevant for all parties, whether a cloud vendor, auditor, user, security provider or customer. Particularly important for those in the financial services or healthcare sector, organisations can use the C5 framework to help guide them towards better awareness and mitigate the vulnerabilities of moving to the cloud.
RingCentral’s commitment to security
Adopting cloud communications can be nerve-wracking, especially when it comes to security and protecting your business conversations. Migrating to the cloud can put you at risk if your providers don’t put measures in place to meet the security standard your business and its customers expect.
Data protection is one of the highest priorities at RingCentral, and our compliance with C5:2020 from the BSI provides our customers with the utmost level of assurance. RingCentral’s unified communications solution, RingCentral MVP, has also achieved three internationally recognised ISO certifications, including ISO 27001, ISO 27017 and ISO 27018 for information security best practices.
Our partnerships with European industry leaders such as Atos and Alcatel-Lucent Enterprise also demonstrate our commitment to protecting the data of our European user base. Adhering to European standards helps us meet local customer needs.
RingCentral customers and partners can use the C5 attestation to understand the security controls we put in place to adhere to the C5 requirements. With a reliable cloud provider such as RingCentral, businesses can significantly reduce risk, enable globally compliant security practices and improve the efficiency of their procurement practices.
Get familiar with the C5
For businesses that have operations in Europe, it is worth paying attention to C5 requirements to prepare for the future. Those already looking to take the next steps to prepare for the requirements of the future should familiarise themselves with the BSI’s requirements.
For further information about RingCentral’s commitment to data privacy and security, visit our Trust Centre, review our Trust Principles or speak to your RingCentral Account Manager.

Originally published Aug 19, 2021, updated Jan 16, 2023